How To Login With A USB Flash Drive Instead Of A Password On Linux Using pam_usb (Fork)
pam_usb is a PAM module that provides hardware authentication for Linux using ordinary USB flash drives, SD cards, MMC, etc.
Using this, you'll be able to login without a password, by simply connecting a USB stick or memory card to your computer. This USB authentication also works when running terminal commands that require superuser - you will not be prompted for a password when using sudo for example.
pam_usb works with any application supporting PAM, such as login managers (GDM, Lightdm, etc.), and su / sudo.
For authentication, pam_usb makes use of the USB flash drive / memory card serial number, model and vendor, as well as optional One Time Pads (OTP). When One Time Pads are enabled (this is enabled by default, but you can disable it), the public user pad file is stored on the USB / memory card in a hidden folder called .pamusb, while the private key is stored in a hidden folder with the same name, stored in the user home directory.
The original developer of this tool seems to have abandoned it, receiving no new commits since April 2016, and no new releases since 2011. Some improvements were made since then, in various repositories. To continue improving pam_usb, the tool was forked, while also including the work that was previously done in other repositories (which include improvements like the UDisk2 port).
pam_usb features:
- Password-less (memory card / USB) authentication. Simply connect the USB stick / memory card that you've configured with pam_usb to login
- Supports USB flash drives, SD cards, MMC, etc.
- Device auto probing. pam_usb doesn't require the USB flash drive to be mounted; it can locate the USB device and access its data directly, using UDisks
- It doesn't need to reformat your USB flash drive
- USB serial number, model and vendor verification
- Supports One Time Pads (OTP) authentication
- Can be used as Two-Factor Authentication, requiring both the USB stick and password to login to your Linux system
- You can use the same memory card / USB stick across multiple machines
There are 3 tools that ship with pam_usb: pamusb-agent which can be used to trigger actions upon device authentication or removal (so for example you can use a command to lock the screen if the device is removed), pamusb-conf which makes setting up pam_usb easier, and pamusb-check which is used to integrate pam_usb's authentication engine within scripts or applications.
pam_usb doesn't currently support adding more than one device per user. For now, pamusb-conf doesn't add devices for users that are already configured. You can track this issue here.
It's worth noting that pam_usb is only used for logging in, and not for unlocking the GNOME Keyring or decrypting private folders. GNOME Keyring doesn't seem to support unlocking by anything other than using the password. So even though you'll be automatically logged in while using pam_usb and the paired USB flash drive is attached, the GNOME Keyring unlock dialog will still be shown, asking you to enter your password to unlock it. The same happens when using fingerprint authentication for example.
I tried this with GDM and LightDM. In both cases at the login screen I had to click on my username and press the Enter key to log in, without having to enter the account password.
[[Edit]] In a comment below, the developer noted that they are trying to find help for a security review of the code. If you can help, please contact them via Github.
USB Related: Create A Bootable USB Drive By Simply Copying The ISO To The USB With Ventoy (Linux And Windows)Install and setup pam_usb (fork)
This pam_usb fork has not been packaged into the official repositories of any Linux distribution. The old, 0.5.0 version (which uses Python2 and Udisks1) is available for a few Linux distributions, but it's missing in most.
The pam_usb fork developer has packaged this pam_usb version for recent Debian and Ubuntu versions (as well as Linux Mint, Pop!_OS, and other Linux distributions based on Debian or Ubuntu), and you can download it from here (you'll only need the libpam-usb package from there).
The pam_usb fork repository also has an Arch Linux / Manjaro PKGBUILD available.
For other Linux distributions you'll need to build it from source.
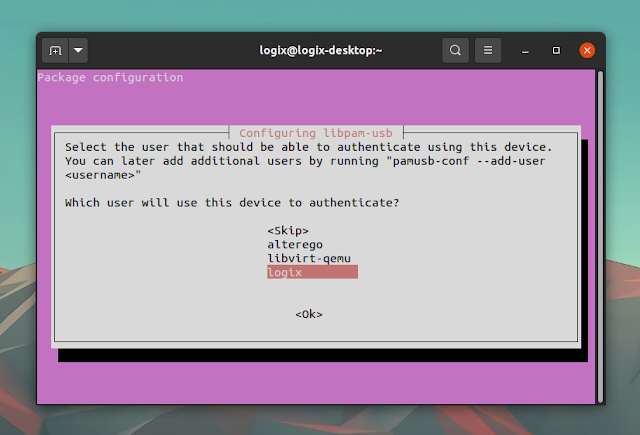
If you're installing pam_usb (fork) from the Debian package provided by its developer, during the installation you'll be prompted to select the device and user:
If that's not the case for you or you want to do this manually later, you can setup pam_usb like this. Plug in a USB flash drive or memory card and run the following command to add your new device as an authentication method:
sudo pamusb-conf --add-device DEVICE_NAMEWhere DEVICE_NAME can be anything you want.
Next, you'll need to add your user to the pam_usb configuration, by using:
sudo pamusb-conf --add-user USERNAMEWhere USERNAME is the user for which you want to enable USB / memory card based authentication.
The username and device info are saved in the /etc/security/pam_usb.conf file.
You can now check the configuration to see if everything is correct by using:
pamusb-check USERNAMEIt's important to note that using the DEB packages provided by its developer, you don't need to configure anything else. But if you're installed pam_usb from source, you'll need to add pam_usb into the system authentication process, as explained here.
For other pam_usb configuration options, see its Configuration wiki page.
Configure pam_usb to lock the screen if the USB stick / memory card is removed (and unlock it once it's plugged back in)
pam_usb can execute commands when the USB stick / memory card is plugged in or removed, with the help of pamusb-agent.
The pam_usb wiki has an example of a configuration for locking the screen when the USB stick / memory card is removed, and unlock it when it's plugged back in. That example no longer works on Gnome (but it should work on other desktop environments, by substituting gnome-screensaver-command with cinnamon-screensaver-command for Cinnamon desktop, mate-screensaver-command for MATE desktop, etc.). [[Edit]] You can also substitute that for xdg-screensaver (part of the xdg-utils package; e.g. xdg-screensaver lock to lock the screen, and xdg-screensaver reset to unlock it).
To get pam_usb to lock the screen if the USB stick / memory card is removed, and unlock once the device is plugged back in, on Linux distributions using systemd (I've only tested this configuration on Gnome with GDM3), I'm using the following configuration (/etc/security/pam_usb.conf):
...................................
<user id="USERNAME">
<device>DEVICE_NAME</device>
<!-- When the user "USERNAME" removes the usb device, lock the screen -->
<agent event="lock">
<cmd>/usr/local/bin/screensaver-lock</cmd>
</agent>
<!-- Resume operations when the usb device is plugged back and authenticated -->
<agent event="unlock">
<cmd>/usr/local/bin/screensaver-unlock</cmd>
</agent>
</user>
...................................Two scripts are used to make this work. /usr/local/bin/screensaver-lock is used for locking the screen, and /usr/local/bin/screensaver-unlock to unlock the screen. Here are their contents.
/usr/local/bin/screensaver-lock:
#!/bin/sh
SESSION=`loginctl list-sessions | grep USERNAME | awk '{print $1}'`
if [ -n $SESSION ]; then
loginctl lock-session $SESSION
fi
/usr/local/bin/screensaver-unlock:
#!/bin/sh
SESSION=`loginctl list-sessions | grep USERNAME | awk '{print $1}'`
if [ -n $SESSION ]; then
loginctl unlock-session $SESSION
fi
In both, replace USERNAME with your username.
You might also like: KDE Connect / GSConnect: How To Lock/Unlock Your Linux Desktop Using An Android Device